一、准备工作
首先需要安装git和cmder工具,下载地址如下:
git for windows
https://git-scm.com/download/win
cmder mini
https://github.com/cmderdev/cmder/releases/download/v1.3.11/cmder_mini.zip
二、启用ldaps
(1)创建ca根证书
1 | openssl genrsa -des3 -out ca.key 4096 |
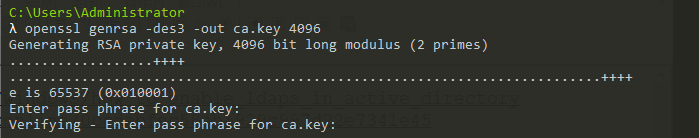
1 | openssl req -new -x509 -days 3650 -key ca.key -out ca.crt |
如下:只需要填Common Name为ad域(jier.site)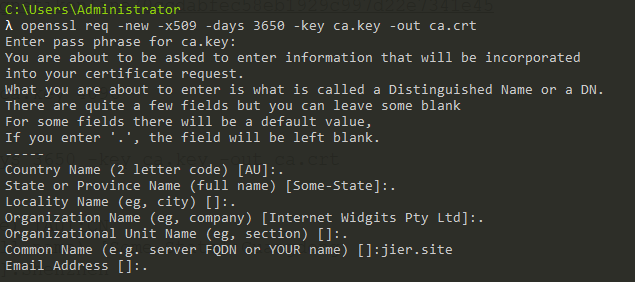
(2)导入ca根证书到本地计算机
执行命令certlm.msc,打开本地计算机的证书控制台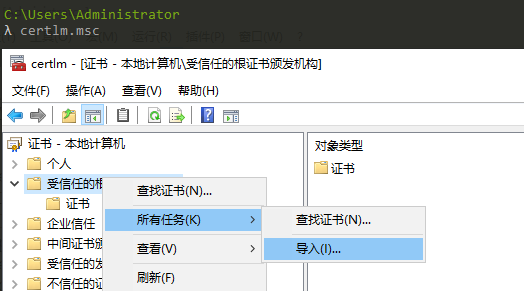
导入ca根证书到”本地计算机\受信任的根证书颁发机构”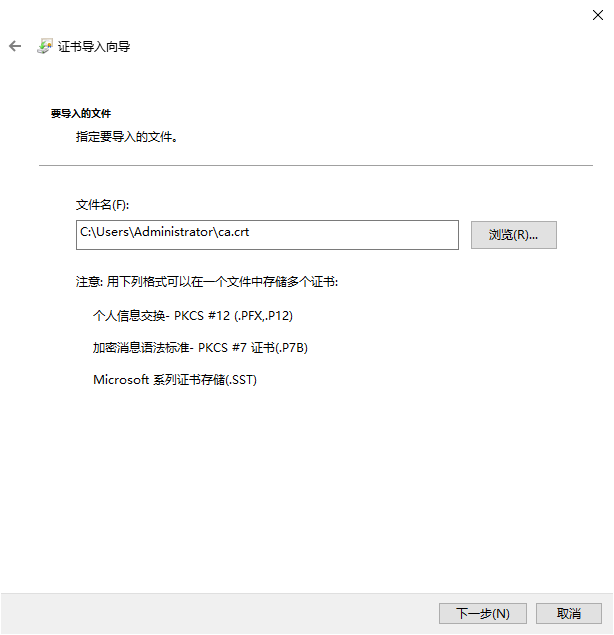
(3)生成request.inf
如下:指定CN为本地计算机全名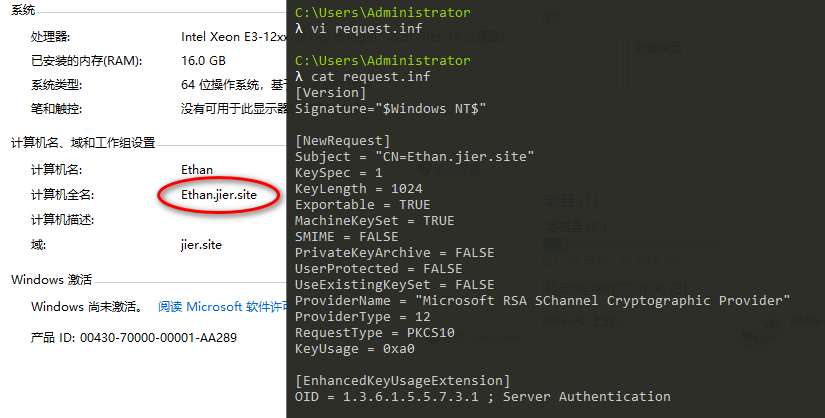
内容如下:
1 | [Version] |
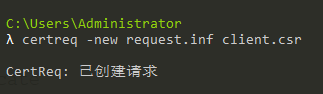
(4)生成client.csr
1 | certreq -new request.inf client.csr |
(5)生成v3ext.txt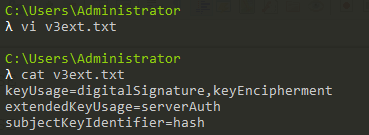
内容如下:
1 | keyUsage=digitalSignature,keyEncipherment |
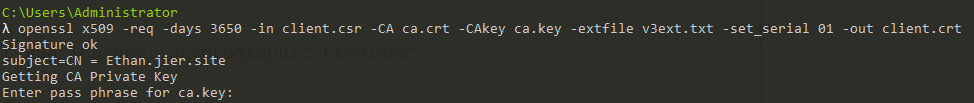
(6)生成client.crt
1 | openssl x509 -req -days 3650 -in client.csr -CA ca.crt -CAkey ca.key -extfile v3ext.txt -set_serial 01 -out client.crt |
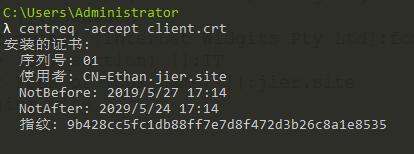
(7)导入客户端证书
1 | certreq -accept client.crt |
(8)生成ldap-renewservercert.txt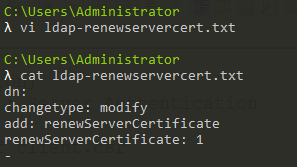
内容如下:
1 | dn: |
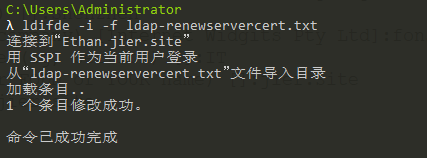
(9)刷新ad域名证书配置
1 | ldifde -i -f ldap-renewservercert.txt |
(10)使用LdapAdmin测试连接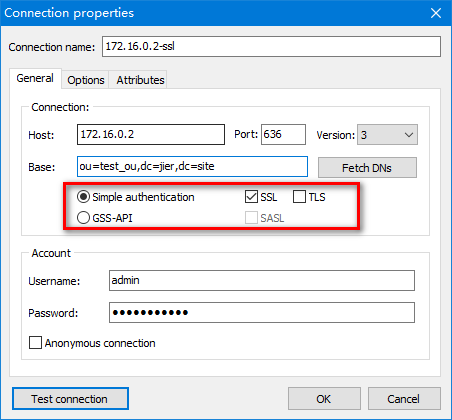
三、参考链接
http://www.javaxt.com/tutorials/windows/how_to_enable_ldaps_in_active_directory
https://gist.github.com/magnetikonline/0ccdabfec58eb1929c997d22e7341e45